

- OPSEC is a term borrowed from the US military. In a military context, it means not talking about (or chatting on IRC about, or posting on Facebook about…) military operations, troop movements, new weapons systems, etc. with people who don’t have a need-to-know, because of the risk of this information falling into enemy spies’ hands.
- In a hacker context, it means not letting information about your identity, geographical location, hacking tools and methods, etc. slip to law enforcement, intelligence agencies, competing hacker groups, or other adversaries. LulzSec is a great case study in terrible OPSEC resulting in a hacking group being taken down hard.
- A security researcher known as The Grugq is the authority on hacker OPSEC. I highly recommend his work on the subject, which can be found here: http://grugq.github.io/presentations/
- SPOILER ALERT: The Grugq’s OPSEC advice can be summed up in one acronym – STFU 😉

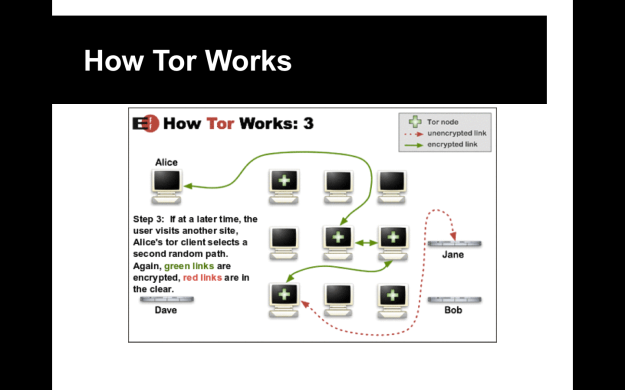
- Tor (The Onion Router) is one of the longest-running anonymity network projects on the Internet. It uses a network of participating nodes to randomly route and anonymize traffic. Tor also can be used to host so-called “hidden services,” sites that aren’t accessible via the normal Internet and only reachable over Tor (the so-called “Dark Net”). Perhaps the best known such site was the Silk Road drug marketplace.
- The easiest way to use it is with the official Tor Browser Bundle, which uses a modified copy of Firefox, but this only protects your web browsing. To protect more of your traffic, you would need to use either:
- 1.) A Tor-centric custom Linux distribution, such as TAILS (famously used by Edward Snowden), Liberté, Whonix, and others
- 2.) A personal router with built-in Tor capabilities, such as the PORTAL router project
- The Invisible Internet Project (I2P) is a newer project that uses a more decentralized, peer-to-peer anonymization approach, known as “garlic routing.” One additional advantage is that, unlike Tor, I2P can route both TCP and UDP traffic, whereas Tor can only route TCP. While, on the surface, it has the potential to be even more secure and hardened against decloaking attacks than Tor, it is a newer project and hasn’t been thoroughly vetted yet. The third iteration of the Silk Road drug market moved to I2P.

- Virtual Private Networks (VPNs) are good enough for hiding your movie pirating or evading region detection, but not good enough for evading law enforcement, as several Anonymous and LulzSec members have found out. Even the ones who claim they never keep logs of your connections. They can be a useful obfuscation means for an attacker, if used in conjunction with an anonymizer like Tor or I2P.
- Proxies and proxifiers are also useful for covering an attacker’s tracks, but again aren’t necessarily built for anonymity, so a wise attacker will use them in conjunction with Tor or another anonymizer.
- For legitimate pen-testers, proxies’ and VPNs’ best use is for evading IDS’s, firewalls, or region restrictions.




- Call me crazy, but if you’re trying to do a zone transfer off my DNS server, that puts you firmly in the “probably a f**king hacker” category and my firewalls and IDS should act accordingly

- Google has a plethora of different operators for finding admin login pages, specific sorts of web technology (like phpBB forums or mySQL instances) you might have exploits for, and other sorts of interesting pages.
- “Robots.txt” is a list of all the pages within a domain that the site owner DOESN’T want search engines to index. Search engines are nice enough to abide by this convention…but it also gives a juicy list of places for hackers to look for stuff like admin portals, diagnostic pages, etc.
- http://www.exploit-db.com/google-dorks/

- For whatever reason, most Unix-like systems have three competing tools for DNS lookups that mostly do the same thing. They are all three developed by the same organization, Internet System Consortium (ISC), who also make BIND, the de facto standard for DNS server software. Nslookup is the oldest, dig and host are newer. Dig is more complex while host is a very simple tool. ISC tried to kill nslookup in favor of dig, but gave up.
- Use whatever the hell you want…or more likely, you’ll just be using some other security tool or script that will use one of them for you.

- Forward lookup = getting the IP address for a given domain name
- Reverse lookup = getting the domain name for a given IP address (take in mind, this doesn’t always work. The name server you’re querying has to be storing PTR records for the particular IP addresses)

- Zone transfer is replicating a DNS server’s entire database of records.

- One person’s useful tool is another’s malicious hacker cyberweapon. Some people even act like firing up Wireshark is evil blackhat sort of shit.
- From here on out, the CEH prep material is extremely tool-centric. If you read the books for this course, you’ll see an especially large volume of tool vomit.
- Look at them, be vaguely familiar with many of them…but really, you only have to know a small number of tools extremely well in order to pass the CEH exam. And we will use those tools extensively in our labs and practical exercises.

- Many of these tools work the same way; they will attempt to brute-force all the different subdomains of a given domain name (usually from a wordlist), brute-force forward or reverse lookups of names and ranges, attempt zone transfers, etc.

- https://github.com/laramies/theHarvester
- Extra credit if you get the reference
- As you’ll see in the upcoming slides, nmap really is the total package. It’s one of the oldest and most versatile security tools out there.



- Netdiscover is super quick and uses ARP, rather than ICMP, in order to identify live hosts on a subnet
- Hping (more properly hping3…but since the CEH exam never gets updated, you may still see it referred to as hping2) is a very versatile and customizable tool for crafting TCP and UDP packets. There’s a lot of overlap between it and nmap, but hping is good for more targetted probing of specific systems and ports.
- Alive6 is a good tool when looking for IPv6 hosts
- Fping is an older than dirt ping sweeper, as is netenum
- Angry IP Scanner is a Windows tool



- Firewalk is specifically a tool for trying to figure out what ports are actually closed on a host and which are just being blocked by a firewall. It uses some traceroute-fu to accomplish that. We’ll discuss it more in the Evasion lesson later in the course.
- Unicornscan is a more advanced host and port scanner, built around being fast and using its own custom-engineered TCP/IP stack. Some like it…I just stick to nmap, personally.
- Dmitry is a quick tool that does port scans…but can also do a little DNS bruting, whois lookups, and can check Netcraft for info on a server
- SuperScan is a Windows TCP port scanner, freeware from McAfee

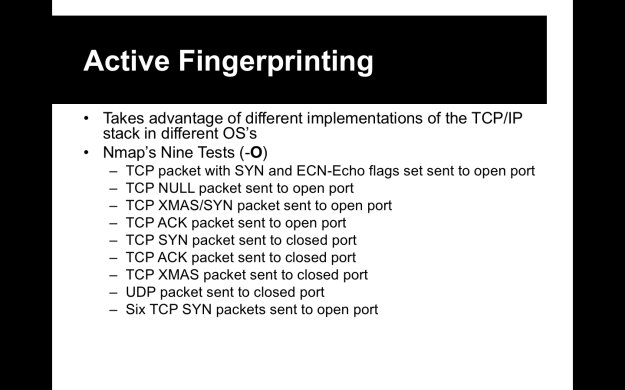
- The idea behind fingerprinting is to look at the packets you receive and look for signs that point to a particular operating system’s TCP/IP stack.
- TCP/IP is regulated by the RFC system…but different OS’s take different approaches and different liberties with implementing them, such as how they respond to illegal flags, TTL values, windows sizes, how they generate session numbers, etc.

- Default TTL (Time To Live) and window sizes vary between Windows and different Unix-like systems.
- Most system have the DF (“Don’t Fragment”) bit set, but if it ISN’T set, it can be a dead giveaway to certain obscure Unix flavors (such as OpenBSD and SCO Unix)
- TOS is of limited usefulness in fingerprinting OS’s.



- p0f requires that you be MiTMing traffic, as it’s a passive scanner.
- Amap is an older scanning tool from the hacker collective THC. Probably not as good as nmap, but maybe worth trying
- Xprobe2 is an active fingerprinting tool
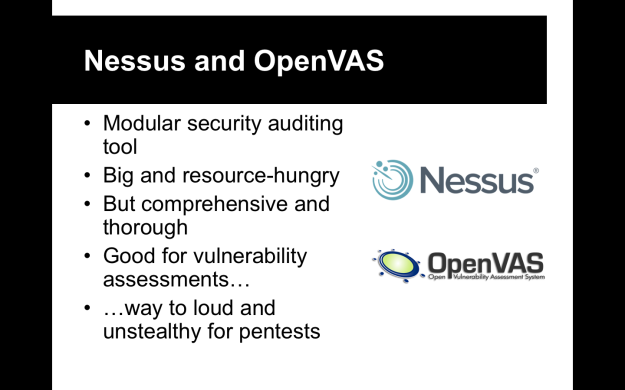
- Nesus used to be an open project, until it was bought up by Tenable Network Security. Tenable closed-sourced it and pissed off lots of folks in the open source and security community.
- In retaliation, the last open version of Nessus (version 2) was forked to formed the OpenVAS (Open Vulnerability Assessment System) project.
- Nessus/OpenVAS scans are like artillery going off on a network…very loud and you will get noticed. Not good for a sneaky pentest, but great if all you need is a vulnerability assessment.


- Most of these scanners are commercial, so we won’t be playing with them. Don’t worry, you won’t need to know any of them for the test.

- Best advice I can give is to install nmap on your own machine or VM, then download the Metasploitable VM and run it. Use nmap to scan Metasploitable with all the different sorts of options and see what sort of results you get.
- OffSec has a good guide for setting up Metasploitable for a lab environment: https://www.offensive-security.com/metasploit-unleashed/requirements/